If you are using mapped network drives, you probably noticed that they are not showing in the apps running with administrator privileges (including cmd and PowerShell). The default User Account Control (UAC) settings don’t allow to access mapped network drives (via net use) from applications running in elevated mode (Run as administrator). This means that when you run the command prompt or a file manager (like Total Commander) with elevated privileges, they won’t display the drive letters of the mounted shared folders.
You may face such a problem if the following conditions are true:
- Network drives are mapped in the user’s session (via GPO or manually via
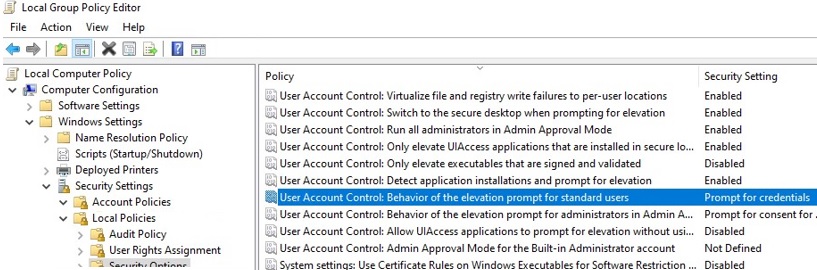
net use); - UAC is enabled on the computer (the GPO parameter User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode is set to default value “Prompt for credentials”);
- The current user has local administrator permissions on the computer and runs the app in the “Run as administrator” mode.
In this case, network drives are displayed in Windows File Explorer and in apps, but are not displayed in any applications running in elevated mode.
In this article we’ll show how to allow access to mapped network drives from the apps running in the elevated mode on Windows 10. This problem occurs both for network drives mapped through Group Policy and for the folders connected by users.
Mapped Network Drives are not Showing in Windows Apps
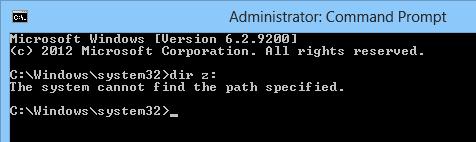
Let’s check that you cannot access the mapped network drive connected in normal mode from an elevated application with UAC enabled. For example, let’s open a command prompt with user permissions and check if you can access the contents of the mapped network drive Z:\.
Net use
Dir z:
The command should list the contents of the shared network folder.
If you open the command prompt in the current session as administrator, and try to access the same drive – you’ll receive the message that the path to the drive has not been found:
The system cannot find the path specified.
This behavior of Windows can cause some inconvenience when you frequently run applications in elevated mode. It is possible to run applications without administrator privileges, but this is not always applicable.
Why does it happen? This peculiarity is related to UAC mechanism for a user with the local administrator privileges. The matter is that when this user log in, two access tokens are created: the first token provides access with disabled administrator privileges (the filtered access token, with which most of the apps are running) and the second is the administrator token with full privileges in the system (all apps approved for elevation by UAC are running in this context).
You can use whoami /all command in two cmd.exe sessions (normal and elevated) of the same user and compare the current privileges, you can see that they are very different. The following table lists the differences in the security groups and current privileges in each session.
| Normal user session | Elevated user session | |
| Security group | Mandatory Label\Medium Mandatory Level???????????? ???????????Label??????????? S-1-16-8192 | Mandatory Label\High Mandatory Level????????????????????????? Label??????????? S-1-16-12288 |
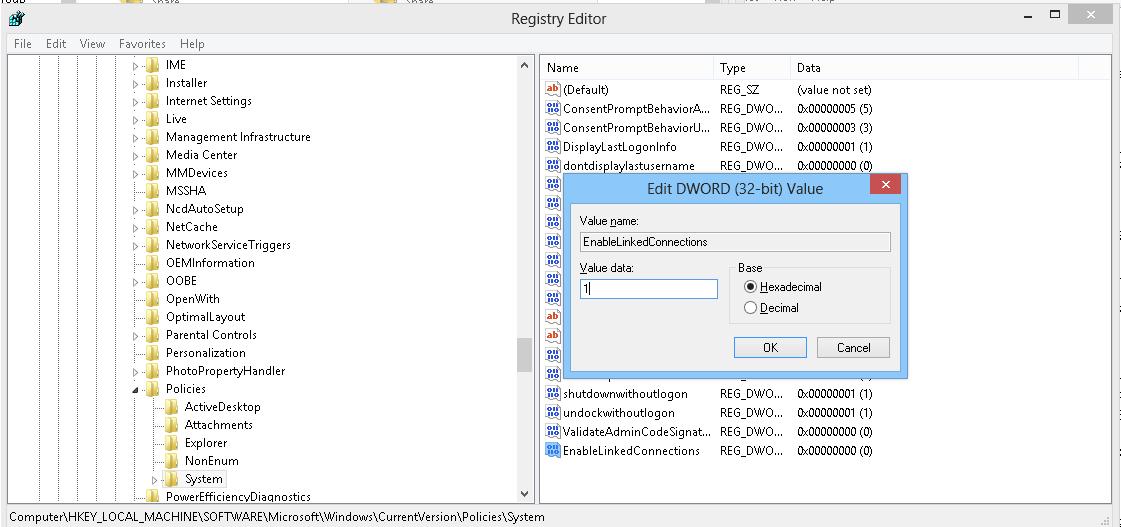
| Privileges | SeLockMemoryPrivilege SeMachineAccountPrivilege SeShutdownPrivilege SeChangeNotifyPrivilege SeUndockPrivilege SeIncreaseWorkingSetPrivilege SeTimeZonePrivilege | SeLockMemoryPrivilege SeIncreaseQuotaPrivilege SeMachineAccountPrivilege SeSecurityPrivilege SeTakeOwnershipPrivilege SeLoadDriverPrivilege 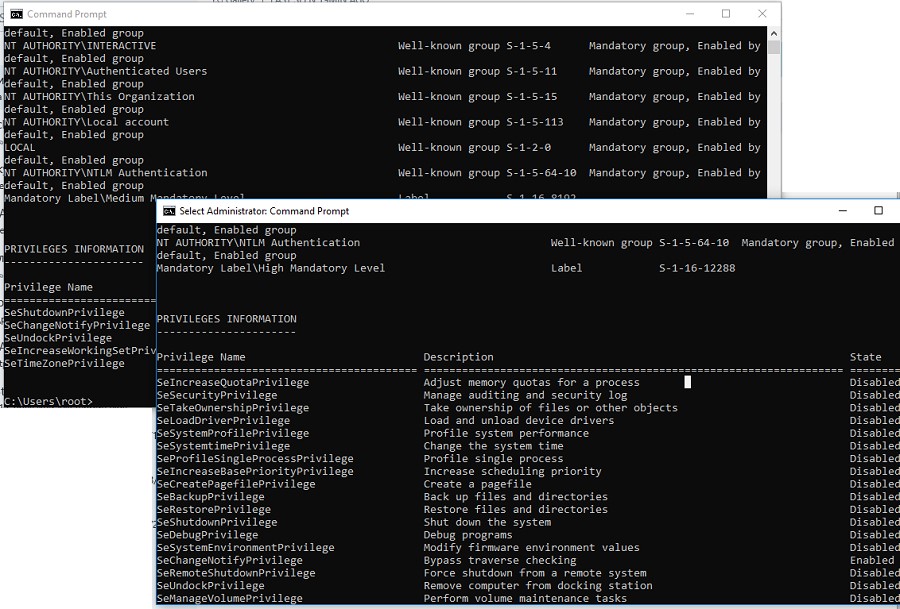 Applications under the same user may be run in two contexts when UAC enabled (privileged and unprivileged). When you map shared network folders, the system creates symbolic links (DosDevices) that store the drive letter mapping to the UNC paths. These links are associated with the current process access token and are not available to other tokens. The reverse problem may also occur: when the user with administrator permissions on the computer is connecting network drives using the Group Policy logon scripts, scheduled tasks or SCCM jobs (which are running with elevated privileges), these drives are not visible to the user in File Explorer (unprivileged process). Tip. You can use a simple trick to run the File Explorer in Windows with admin rights (elevated). As a workaround, you can mount network drives from the elevated command prompt using the commands: Enablelinkedconnections: Enabling Mapped Drives in the Elevated AppsThere is an easier solution. To implement it, you have to make some changes to the registry:
After restarting the computer, make sure that the user can see the mapped network drives in programs running with admin rights. The reverse statement is true: all network drives mapped in the elevated mode will also be available in the unprivileged user session. This works on all Windows versions starting from Vista to Windows 10/Windows Server 2019. Note. Unfortunately there is no GPO setting to enable the EnableLinkedConnections mode. In order to apply this setting on the domain computers you need deploy this registry parameter through GPP. How it works? After you enabled the EnableLinkedConnections registry parameter, LanmanWorkstation and LSA (lsass.exe) will check for a second access token associated to the session of the current user. If this token is found, the list of the mapped network drives will be copied from one token to another. Thus, the network drives mapped in the privileged mode will be visible in the normal mode, and vice versa. Tip. As an alternative solution, you can create a symbolic link to the target shared network folder. For example, as follows:
You can access this drive in both normal and elevated mode. It should be noted that one of the drawbacks of this method is that you access the shared folder as a current user. It is impossible to use the account of another user as in the case of After enabling the EnableLinkedConnections parameter, mapped drives will also become available from the Scheduled Tasks launched under the current user. If the task is run as LocalSystem or another user, the mapped network drives of the current user will be unavailable. previous post Shrinking VMDK Virtual Disk Size on VMWare ESXi
新版的欧美在线视频,精品国偷自产国产一区,亚洲精品福利视频网站,日韩一区二区三区观看
丰满少妇在线播放bd日韩电影|
欧美一区二区三区思思人|
精品国产伦一区二区三区观看方式|
国产精品久久毛片|
亚洲 欧美综合在线网络|
亚洲精品美国一|
成人免费视频视频在线观看免费|
麻豆精品国产91久久久久久|
国产成人福利片|
欧美一区二区三区思思人|
欧美大尺度电影在线|
欧美丰满嫩嫩电影|
精品国产乱码久久久久久1区2区|
亚洲国产裸拍裸体视频在线观看乱了|
91麻豆国产自产在线观看|
久久日一线二线三线suv|
精品中文av资源站在线观看|
日本中文一区二区三区|
日本亚洲欧美天堂免费|
天天综合网 天天综合色|
色婷婷综合五月|
91麻豆产精品久久久久久|
www亚洲一区|
免费成人美女在线观看|
人人爽香蕉精品|
国产精品系列在线观看|
国产美女精品人人做人人爽|
成人伦理片在线|
日本在线播放一区二区三区|
日本大香伊一区二区三区|
国产麻豆精品视频|
成人av电影在线网|
日韩精品一二三|
精品国产一二三|
欧美日韩高清在线|
久久先锋影音av鲁色资源网|
国产精品一区二区免费不卡|
麻豆91精品视频|
亚洲成人在线免费|
国产精品久久久爽爽爽麻豆色哟哟|
亚洲激情网站免费观看|
亚洲精品网站在线观看|
日韩精品资源二区在线|
亚洲欧美激情一区二区|
亚洲丝袜美腿综合|
成人永久看片免费视频天堂|
国产精品免费人成网站|
精品一区二区三区视频在线观看|
91精品国产一区二区三区|
亚洲女厕所小便bbb|
日韩欧美激情一区|
奇米在线7777在线精品|
91久久香蕉国产日韩欧美9色|
精品国产一二三区|
视频一区二区欧美|
亚洲国产欧美一区二区三区丁香婷|
一区二区三区日韩欧美精品|
极品尤物av久久免费看|
国产传媒久久文化传媒|
青草国产精品久久久久久|
久久九九国产精品|
国产日产欧产精品推荐色|
一区二区三区欧美视频|
91精品中文字幕一区二区三区|
成人妖精视频yjsp地址|
最新欧美精品一区二区三区|
精品在线免费观看|
自拍av一区二区三区|
久久精品欧美一区二区三区不卡|
精品日韩99亚洲|
亚洲国产精品影院|
一区二区三区中文字幕精品精品|
aaa欧美色吧激情视频|
亚洲视频一区在线观看|
午夜精品久久久久久久99水蜜桃|
精品成人一区二区三区|
香蕉乱码成人久久天堂爱免费|
国产欧美综合在线|
在线精品亚洲一区二区不卡|
色综合网站在线|
欧美日韩成人在线一区|
久久精品99国产国产精|
国产日韩欧美不卡|
国产视频一区二区在线观看|
精品日韩欧美一区二区|
麻豆久久久久久|
欧美日韩高清一区二区三区|
欧美在线三级电影|
国产成人三级在线观看|
亚洲欧洲无码一区二区三区|
久久久久久免费|
久久精品久久久精品美女|
色婷婷久久久综合中文字幕|
九九精品视频在线看|
日韩不卡手机在线v区|
91搞黄在线观看|
91丝袜美腿高跟国产极品老师|
国产亚洲精品超碰|
亚洲资源中文字幕|
久久99九九99精品|
久久综合资源网|
欧美人妇做爰xxxⅹ性高电影|
色就色 综合激情|
91在线观看高清|
久久综合成人精品亚洲另类欧美|
成人精品一区二区三区中文字幕|
亚洲免费观看在线观看|
精品亚洲成av人在线观看|
在线观看av一区二区|
91蜜桃视频在线|
欧美日韩精品一二三区|
在线中文字幕一区|
另类小说综合欧美亚洲|
中文字幕成人网|
天天做天天摸天天爽国产一区|
欧美日韩一区二区三区在线看|
精品一区二区在线免费观看|
一区二区欧美在线观看|
国产精品中文字幕欧美|
成人午夜av电影|
国产精品嫩草影院com|
国产成人综合精品三级|
国产91高潮流白浆在线麻豆|
51精品国自产在线|
亚洲成av人片一区二区三区|
国产激情视频一区二区在线观看|
久久国产精品99久久久久久老狼|
最新日韩在线视频|
亚洲综合清纯丝袜自拍|
国产清纯白嫩初高生在线观看91|
亚洲视频综合在线|
一区二区三区四区五区视频在线观看|
7777精品伊人久久久大香线蕉完整版|
国产成人精品亚洲日本在线桃色|
日本道色综合久久|
夜夜精品浪潮av一区二区三区|
国内精品伊人久久久久av影院|
五月天久久比比资源色|
亚洲精品成人在线|
婷婷综合五月天|
成人av高清在线|
日本乱码高清不卡字幕|
九九在线精品视频|
久久久久久99久久久精品网站|
中文字幕不卡一区|
国产精品一区在线|
天天影视网天天综合色在线播放|
99久久99久久精品免费看蜜桃|
欧美精品在线一区二区三区|
99久久精品免费看国产免费软件|
日本不卡在线视频|
欧美色视频在线观看|
成人精品视频一区二区三区|
日韩午夜电影在线观看|
26uuu精品一区二区|
麻豆精品久久久|
亚洲成va人在线观看|
91蝌蚪国产九色|
91蜜桃传媒精品久久久一区二区|
成人一二三区视频|
午夜欧美2019年伦理|
成人在线一区二区三区|
老司机精品视频线观看86|
久久成人久久鬼色|
亚洲免费伊人电影|
久久综合一区二区|
免费在线看一区|
亚洲高清中文字幕|
欧美成人vps|
视频一区欧美精品|
一区二区高清视频在线观看|
色88888久久久久久影院野外|
一区二区三区日韩欧美精品|
国产日韩欧美综合在线|
99re这里都是精品|
国产精品乱码妇女bbbb|
亚洲午夜成aⅴ人片|
国产精品天干天干在观线|
亚洲激情av在线|
国产精品一区二区不卡|
91麻豆成人久久精品二区三区|
国产欧美视频一区二区|
97久久精品人人爽人人爽蜜臀|
色欧美88888久久久久久影院|
高潮精品一区videoshd|
水蜜桃久久夜色精品一区的特点|
亚洲自拍偷拍欧美|
久久午夜羞羞影院免费观看|
天堂av在线一区|
欧美日韩久久一区|
日韩午夜电影在线观看|
一区二区在线观看视频在线观看|
日韩不卡一区二区三区|
日韩欧美国产成人一区二区|
国产剧情一区二区三区|
欧美videofree性高清杂交|
久久国产精品第一页|
麻豆久久一区二区|
亚洲国产cao|
亚洲人精品午夜|
|


4 comments
Great! Well explained!
I remember having a hard work to understand why my mapped drives were not appearing in the elevated prompts… Until I found a technet post that saved my life lol
I faced this issue before and had to change the registry parameter to solve it.
Now is more clear and understood.
Many thanks!
did not work for Quickbooks Desktop Enterprise
This did not work for me. Environment: VirutalMachine: Guest: Win 10 Pro, Host: Win 10 Pro, Mapped Network Drives: “\\vmware-host\Shared Folders\*”.
I found that by creating a batch file that causes and elevated “Administrator: Command Prompt” and a All users Startup (shell:common startup”) I am able to automate the mapping. Note that the normal File Manager mapping works.
The code to get an elevated command prompt can be found at: https://stackoverflow.com/questions/11525056/how-to-create-a-batch-file-to-run-cmd-as-administrator